Secure Remote IoT Access With SSH And AWS: Your Guide
Connecting to your devices from afar, especially when they are part of the Internet of Things, has become a very big deal. Think about all the little gadgets and sensors out there. You want to make sure you can reach them, check on them, and keep them working right, no matter where you are. This is where the idea of remoteiot ssh aws comes into play. It's about getting to your smart things securely, using tools you already trust, and doing it all with the help of Amazon Web Services.
For anyone who works with cloud computing, smart devices, or tiny computers like the Raspberry Pi, getting good at this kind of remote connection is a really useful ability. As new technology keeps showing up, being able to look after and get to devices that are far away has grown more important than ever. This piece will show you how to set up a safe way to link your Raspberry Pi to AWS, using what's called a virtual private cloud and secure shell connections, too it's almost like having your device right next to you.
The combination of remoteiot, virtual private cloud (VPC), secure shell (SSH), Raspberry Pi, and Amazon Web Services (AWS) makes a very solid way to work with things from a distance. It’s not just a bunch of technical words; it’s your way to safely get to and look after your smart devices from any spot on Earth, using AWS. This whole setup, you know, gives a complete way to handle IoT devices safely and effectively, which is pretty neat.
- Aishah Tiktok
- What Car Does Mark Davis Drive
- What Does Tom Brady Own
- Who Is The Youngest Football Player Married
- What Businesses Does Patrick Mahomes Own
Table of Contents
- Why Remote IoT Access Matters
- The Key Pieces: RemoteIoT, SSH, and AWS
- AWS IoT Secure Tunneling Explained
- Getting Your Raspberry Pi Ready for AWS
- Making the SSH Connection: Step-by-Step
- Remote Development with VS Code and SSH on AWS
- Good Ways to Manage Remote IoT Devices Safely
- Frequently Asked Questions
- Final Thoughts
Why Remote IoT Access Matters
Having the ability to get to your IoT devices from far away is more than just handy; it’s a must-have for lots of situations. Imagine you have sensors spread out in a big area, or maybe smart home devices in different buildings. You can't just walk up to each one every time you need to check something or fix a small issue. So, this remote access saves a lot of time and effort, you know, making things much smoother.
Security is a very big part of this, too. When you open up your devices to the internet, you need to be really careful about who can get in. Bad actors are always trying to find weak spots. Using something like remoteiot ssh aws helps put a strong lock on those connections, keeping your data and devices safe from unwanted visitors. It's like putting a strong guard at the door, that is, for your digital things.
Also, being able to get to devices remotely means you can keep them updated and running at their best. If there's a new software fix or an adjustment needed, you can push it out from your desk, no matter where the device is. This keeps your IoT setup working well and stops small problems from becoming big ones, which is pretty useful.
- Who Will Be In The Super Bowl 2025
- What Is Joe Burrows Salary
- Which Nfl Owner Says His Girlfriend Likes His Smile
- Who Is Kristin Fishers Husband
- What Car Does Dolly Parton Drive
The Key Pieces: RemoteIoT, SSH, and AWS
To really get how remoteiot ssh aws works, it helps to break down the main parts. Each one plays a specific part in making sure you can talk to your distant devices safely and without too much trouble. It's like building something with different kinds of blocks, and each block has its own job, so.
What is RemoteIoT?
RemoteIoT simply means managing and interacting with Internet of Things devices that are not physically close to you. These could be anything from a smart thermostat in another town to a network of environmental sensors in a far-off field. The challenge is always how to connect to them reliably and, more importantly, safely. This is where the "remote" part of remoteiot ssh aws really comes in, you know, making distant things feel close.
A Look at SSH
SSH, or Secure Shell, is a method for connecting to a computer over an unsafe network in a very safe way. It lets you run commands, move files, and even set up remote development environments as if you were sitting right in front of the machine. When it comes to remoteiot, SSH gives you that direct line to your device, but with a strong layer of protection. For example, you need the location of the private key (.pem file), the username, and the public DNS name or IPv6 address to connect, which makes it pretty secure.
You can use SSH to connect to your Linux instance and run commands, or use SSH to move files between your local computer and your instance. This basically means, you can ssh into any remote instance on any cloud service and get a VS Code instance up and running with absolutely no setup required on the instance! It’s really quite helpful, that is, for quick work.
AWS and IoT Devices
Amazon Web Services (AWS) provides a wide range of services that are perfect for IoT setups. It gives a dependable place for your devices to connect to, a safe spot for their data, and even ways to handle those connections. AWS IoT Core, for instance, is a service that lets billions of IoT devices and trillions of messages connect to AWS services without much trouble. This makes AWS a very central piece of the remoteiot ssh aws puzzle, you know, tying everything together.
AWS IoT Secure Tunneling Explained
One of the coolest things AWS offers for remote IoT access is AWS IoT Secure Tunneling. This service helps you get to devices that are behind firewalls or in private networks without needing to open up specific ports on those networks. It creates a secure, encrypted path directly to your device, making it much safer than traditional methods. It's a bit like having a secret, protected passageway directly to your device, rather.
To use this, you open a tunnel. You can open a secure tunnel using the AWS Management Console, the AWS IoT API reference, or the AWS CLI. You can optionally set a destination name, but it's not needed for every guide. If you set the destination, secure tunneling will automatically send the access token to the remote device using MQTT. This is important because the firewalls that the remote device is behind must let outbound traffic on port 443. The tunnel you make will use this port to connect to the remote device, which is how it gets through.
You also need to have an IoT thing created in the AWS IoT registry, for example, "remotedevice1." This "thing" is how your remote device is seen in the cloud. For more information on this, you can look up how to register a device in AWS IoT. This whole process makes sure that the connection is not only private but also that only authorized devices can join the tunnel, which is a good thing.
Getting Your Raspberry Pi Ready for AWS
Setting up your Raspberry Pi to work with AWS for remote access involves a few steps. First, you need to make sure your Raspberry Pi has an operating system installed, like Raspberry Pi OS, and that it's connected to the internet. Then, you'll want to get it registered as an "IoT thing" in your AWS IoT account. This gives your Pi an identity in the cloud, so.
Next, you'll need to install the necessary AWS IoT Device SDKs or tools on your Raspberry Pi. These tools help your Pi communicate with AWS IoT Core and take part in secure tunneling. There are guides available, like "Panduan lengkap Raspberry Pi di AWS dengan Windows download," which can help you get started with this. It's about getting the right software on your Pi so it can talk to AWS, you know.
You also need to set up the proper security certificates and keys on your Raspberry Pi. These are like digital passports that prove your device is who it says it is when it tries to connect to AWS. This is a very important step for keeping your connections safe and making sure only your devices can link up. It's a bit of work, but it really pays off for security, apparently.
Making the SSH Connection: Step-by-Step
Once your Raspberry Pi is set up with AWS IoT, connecting to it using SSH becomes much simpler, especially with AWS IoT Secure Tunneling. The tunnel acts as a bridge, letting your SSH client on your local computer talk directly to your Raspberry Pi, even if it's behind a firewall. This is a rather clever way to get around network restrictions.
To connect to your instance using an SSH client, you open a terminal window on your computer. Then, you use the SSH command to connect to the instance. You need the details about your instance that you gathered as part of the prerequisites. For example, you need the location of the private key (.pem file), the username, and the public DNS name or IPv6 address. The following are example commands you might use, so it's pretty straightforward once you have the info.
The SSH command usually looks something like `ssh -i /path/to/your/key.pem username@public_dns_name`. The `-i` part points to your private key file, which is essential for proving who you are. The username is often `ec2-user` for EC2 instances, or `pi` for a Raspberry Pi, and the public DNS name is how you find your device on the internet. This whole process is your ticket to securely accessing and managing your IoT devices from anywhere in the world using Amazon Web Services (AWS), which is a big deal.
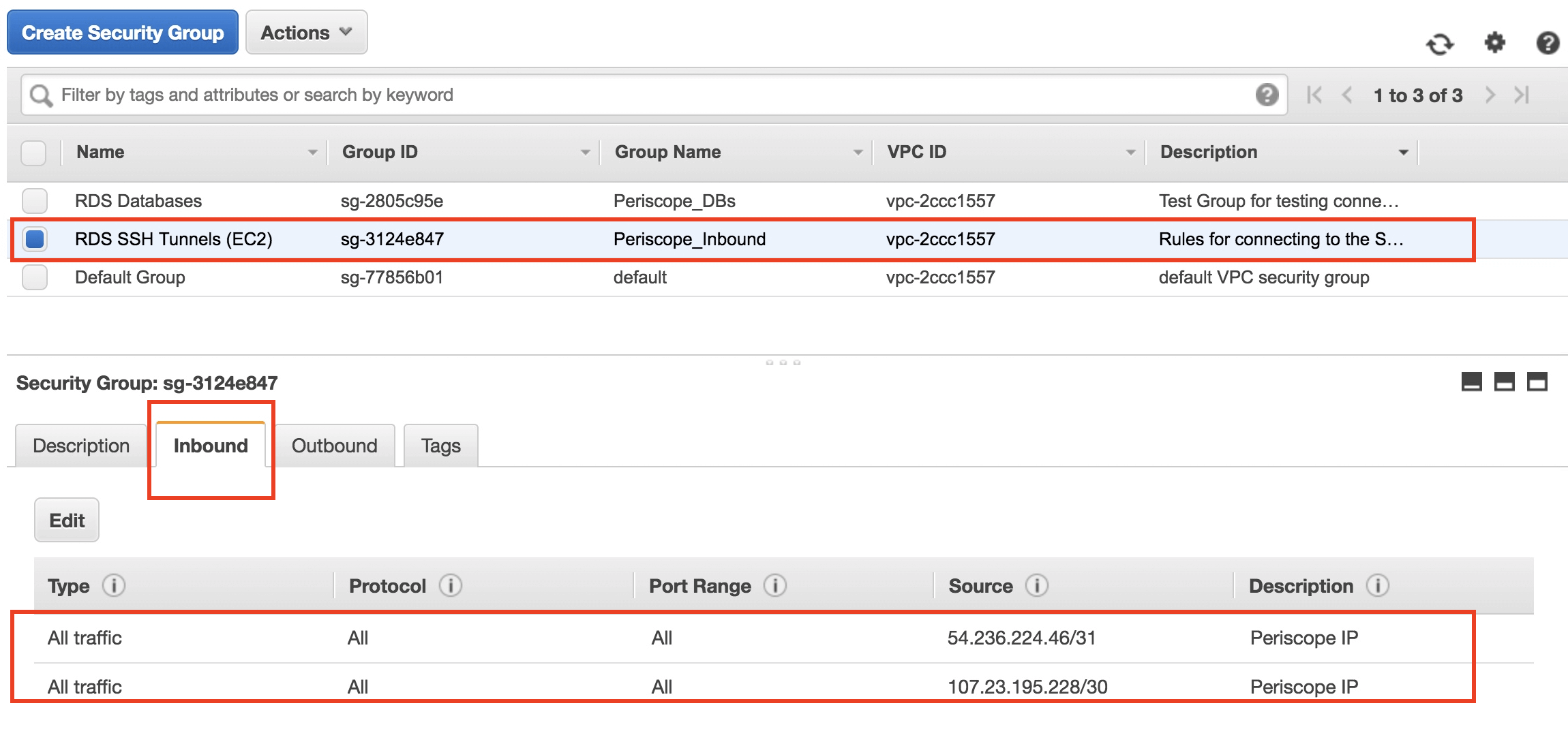
Enabling inbound SSH traffic to a workspace means you need to add a rule to allow incoming SSH traffic to one or more Linux workspaces. You must have the public or private IP addresses of the devices that need SSH connections to your workspaces. For example, you can specify the public IP addresses of devices outside your virtual private cloud (VPC) or the private IP address of another EC2 instance. This makes sure that only trusted sources can try to connect, you know, adding another layer of security.
Remote Development with VS Code and SSH on AWS
Beyond just running commands, you can also do full-blown software development on your remote IoT devices or AWS instances using Visual Studio Code and its Remote-SSH extension. This is a game-changer for developers, as it lets you write code, debug, and test directly on the remote machine as if the code were local. It's pretty amazing how seamless it feels, actually.
Visual Studio Code’s remote development extensions are great and let you openly develop in a container or on a remote computer through SSH. Simply connect to it, and your Visual Studio Code window will attach to the running instance. I will be showing how to use the Remote SSH extension in Visual Code and to SSH into an AWS EC2 instance using it. You copy the username@publicdns, which you are able to see in the instance details. This makes setting up remote development on an AWS EC2 instance using Visual Studio Code and SSH quite simple. This guide gives clear steps to connect via SSH and start coding remotely on EC2 with ease, so you can get to work quickly.
You'll be able to run Telescope in development on a remote machine with VS Code just like if the source code was local. This documentation is based on remote development over SSH. Telescope is a tool for tracking blogs around Seneca's open source development. This capability means you don't need to transfer large codebases back and forth, and you can use the processing power of your AWS instance or the specific environment of your Raspberry Pi for development. It really speeds things up, you know, when you're working on projects that involve remote devices.
Good Ways to Manage Remote IoT Devices Safely
When you're dealing with remote IoT devices and using SSH with AWS, following some good practices makes a big difference in keeping things safe and running smoothly. It's not just about setting it up once; it's about keeping it secure over time. For instance, always use strong, unique passwords or, better yet, key-based authentication for SSH. This is a very basic but very important step, you know, for keeping bad guys out.
Regularly update your device's software and operating system, as well as any AWS tools you're using. Software updates often include security fixes that close potential weaknesses. It’s like keeping your house locked and checking the locks often. Also, limit who has access to your AWS accounts and SSH keys. Only give access to people who absolutely need it, and use AWS Identity and Access Management (IAM) to control permissions very carefully. This helps a lot, in some respects, with keeping things tight.
Monitoring your connections and device activity is another smart thing to do. AWS provides logging and monitoring tools that can alert you to unusual activity, which might mean someone is trying to get in without permission. By understanding the main ideas, taking on the suggested good ways of doing things, and using AWS services, organizations can set up a safe, good, and growing way to handle remote IoT devices. This kind of ongoing care is what really makes your remoteiot ssh aws setup strong for the long haul, that is, for reliable operation.
Frequently Asked Questions
People often ask about how to get to their IoT devices from far away. It's a common concern, especially with all the talk about security these days. Here are some answers to questions that come up a lot, so.
How do I securely access my IoT devices remotely?
You can get to your IoT devices safely from a distance by using services like AWS IoT Secure Tunneling along with SSH. This makes a private, encrypted connection right to your device, even if it's behind a firewall. It's a bit like having a secret pathway that only you can use, which is pretty neat.
What is AWS IoT Secure Tunneling?
AWS IoT Secure Tunneling is a service that helps you connect to devices that are not directly reachable on the public internet. It creates a secure, encrypted tunnel between your computer and your IoT device, letting you use standard protocols like SSH without opening up network ports. It's a very helpful tool for remote access, you know, keeping things private.
Can I use SSH with Raspberry Pi and AWS?
Yes, you absolutely can use SSH with your Raspberry Pi and AWS. By setting up your Raspberry Pi as an AWS IoT "thing" and using AWS IoT Secure Tunneling, you can establish an SSH connection to your Pi from anywhere. This lets you manage and develop on your Raspberry Pi as if it were right next to you, which is very convenient.
Final Thoughts
Getting a handle on remoteiot ssh aws really gives you a lot of freedom and peace of mind when it comes to managing your Internet of Things devices. It’s about more than just connecting; it’s about connecting safely and efficiently, no matter the distance. The methods we’ve talked about today, from using AWS IoT Secure Tunneling to setting up remote development with VS Code, show you a clear path to achieving this. Learn more about secure connections on our site, and check out this page AWS IoT Secure Tunneling documentation for more in-depth details. As of late 2023, these practices remain the go-to for many working with remote devices.
- What Religion Is Brett Baier
- What Is Sean Hannitys Level Of Education
- Where Is The Super Bowl 2025 Location
- How Much Of Raiders Does Tom Brady Own
- Who Is The Highest Paid Qb In Nfl History

AWS SSH Security Group Configuration | Sisense for Cloud Data Teams
AWS SSH Security Group Configuration | Sisense for Cloud Data Teams

Mastering Iot Ssh Download Aws A Comprehensive Guide - ACCDIS English